Chain key technology is at the heart of the Internet Computer blockchain to make it run at speed much faster than its counterparts like Bitcoin, Ethereum, etc.
Essentially, it represents a 48-byte public key that allows the blockchain to work correctly and can be used to rely on for the correctness of the entire state of the Internet Computer.
Before we decode the above, let’s talk about how the code is written on the internet computer. The canisters (like smart contracts in other chains) contain a program code that is uploaded by developers to the internet computer. Canisters contain the program code and as well as the state. These canisters are replicated on all nodes in a subnet on the Internet computer. A subnet represents a group of nodes and Internet Computer currently has around 20 of these subnets, running together many nodes.
There are two types of operations that can be performed on a canister code, one is a query, and the other is an update operation. The query operation returns the result back in milliseconds since it doesn’t update any state. Although this speed comes with a tradeoff with security and a certified query response will take more time than that. The update operation updates the state of a canister and hence takes more time usually in seconds and requires the nodes in a subnet to run the code inside the canister when instructed by the user or other canisters and then those nodes agree upon the result of that computation by a protocol (containing consensus mechanism, and certifying the result of computation of that canister code in a subnet, etc).
Replicating and running a canister code on multiple nodes in a subnet avoids centralization. At least 2/3rd of nodes in a subnet need to agree upon and sign the output using their individual secret key shares of their subnet’s public key (at least 3/4th of key shares are needed to form the subnet’s public key) for finalization of the result of the canister code that was run. This is where that 48-byte public chain key comes into play which determines the correctness of all computations that were made and is alone sufficient to guarantee correctness as compared to the job that more than 400 GB (and growing) of data does in the case of Ethereum clients.
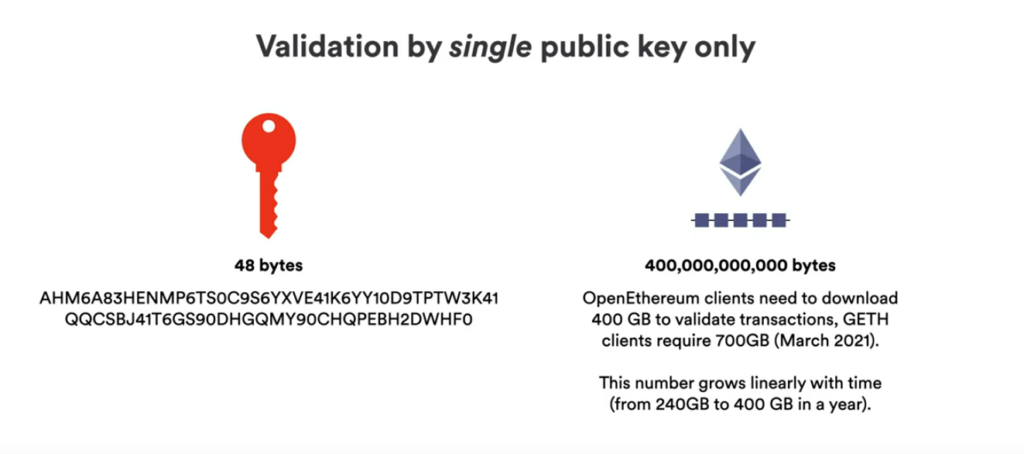
Every subnet has a public chain key of 48 bytes assigned to them by NNS (Network Nervous System) which is a special subnet that generates those keys of various subnets along with the certificates for them. The single public key of the NNS represents the public chain key of the entire Internet Computer!
NNS takes care of governance of all these subnets and has actions like creating a subnet, adding/removing nodes from subnets, generating public keys of the subnets, and key shares of individual nodes in those subnets, certificate on the public key on the subnet, etc. You can interact with NNS at https://nns.ic0.app/ . The generation of individual key shares of nodes of the subnet public key of a subnet takes place using a process called NiDKG (Non-Interactive Distributed Key Generation) which can be covered in the upcoming posts.
Now whenever a user receives a response from the canister code that was run, it is signed by the subnet’s key and also contains the certificate that was generated by NNS for that subnet. The user now just needs the public chain key of the NNS which can be used to validate the certificate of the subnet’s public key received and further validate the certificate on the message on the response user gets back from the subnet. In short, the public key of NNS is sufficient to validate the response user gets from the subnet which ran its canister code.
This post is an effort to explain a very important concept of the Internet Computer which is Chain Key Technology which is the reason for the fast speed (web speed) of running code and applications on the Internet Computer.
Any feedback or comments can be shared here — nanditmehra123@gmail.com
Follow me on https://twitter.com/nanditmehra for more blockchain and crypto-related stuff.
Pretty in-depth insight!
I just admire the author of this article, well-rounded, glamorous, humorous, and charismatic!Even envious!
Support IC and IC Drive!
OK, that’s it!